御网杯
御网杯
kunkunmisc
misc1
考察知识点:word隐写
wps打开,ctrl+A全选,调换颜色即可
flag{HNCTF9090AS9nbg87600hn77hn88}
misc2
考察知识点
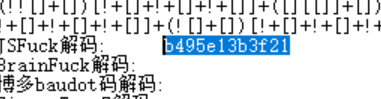
编码1:BrainFuck解码
编码2:JSFuck编码
编码3:ook解密
在线网址:[Brainfuck/Ook! Obfuscation/Encoding splitbrain.org]
misc3
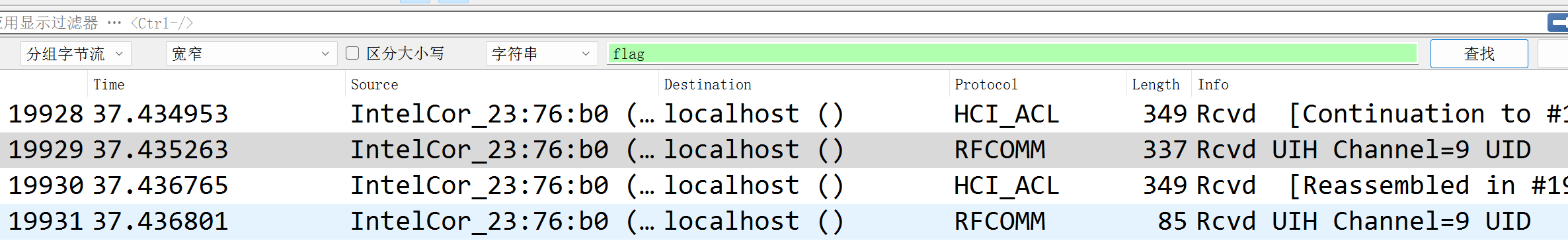
分组字节流搜索flag,我们可以发现在长度为337,349,85的包里搜索到flag
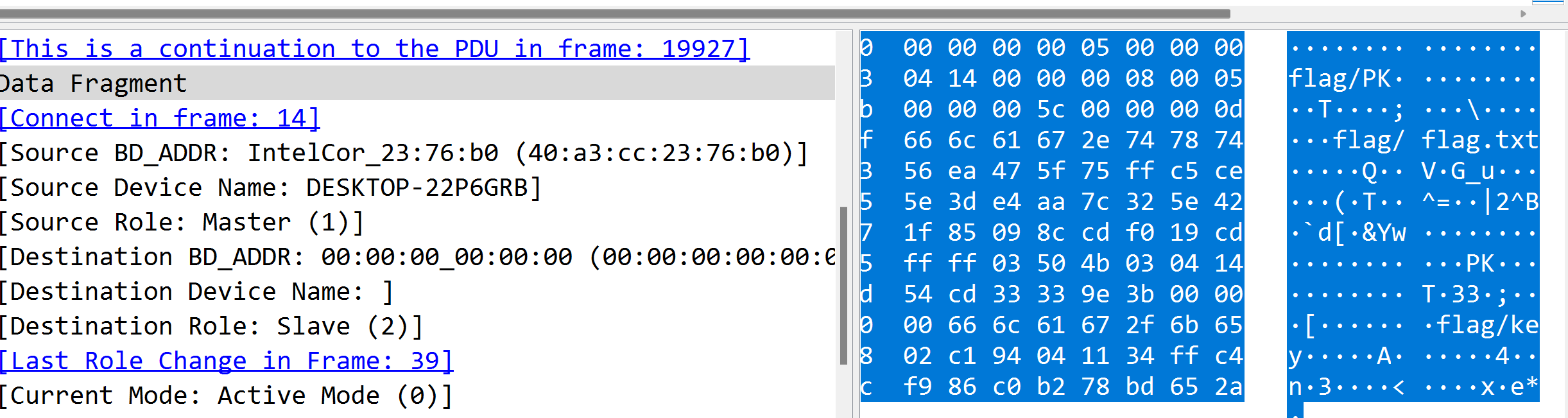
提取其16进制,保存为压缩包,打开我们可以发现flag.txt和key
flag:
10004583275926070044326083910251708233320797779355779208703097816305188140191914132269450797
4e94dcdb6de87e65d263419ec45aec93e8a2e1d386b31fb804e0f02366df44dbe86a8a7c462d
key
5216294695211820293806247029887026154798297270637676463374801674229881314620340407569315152
28f8bdbc16de4850e05579acf33c8aa08ac3d9e6e3822b8c3081c04700eb25b88a08eb457550
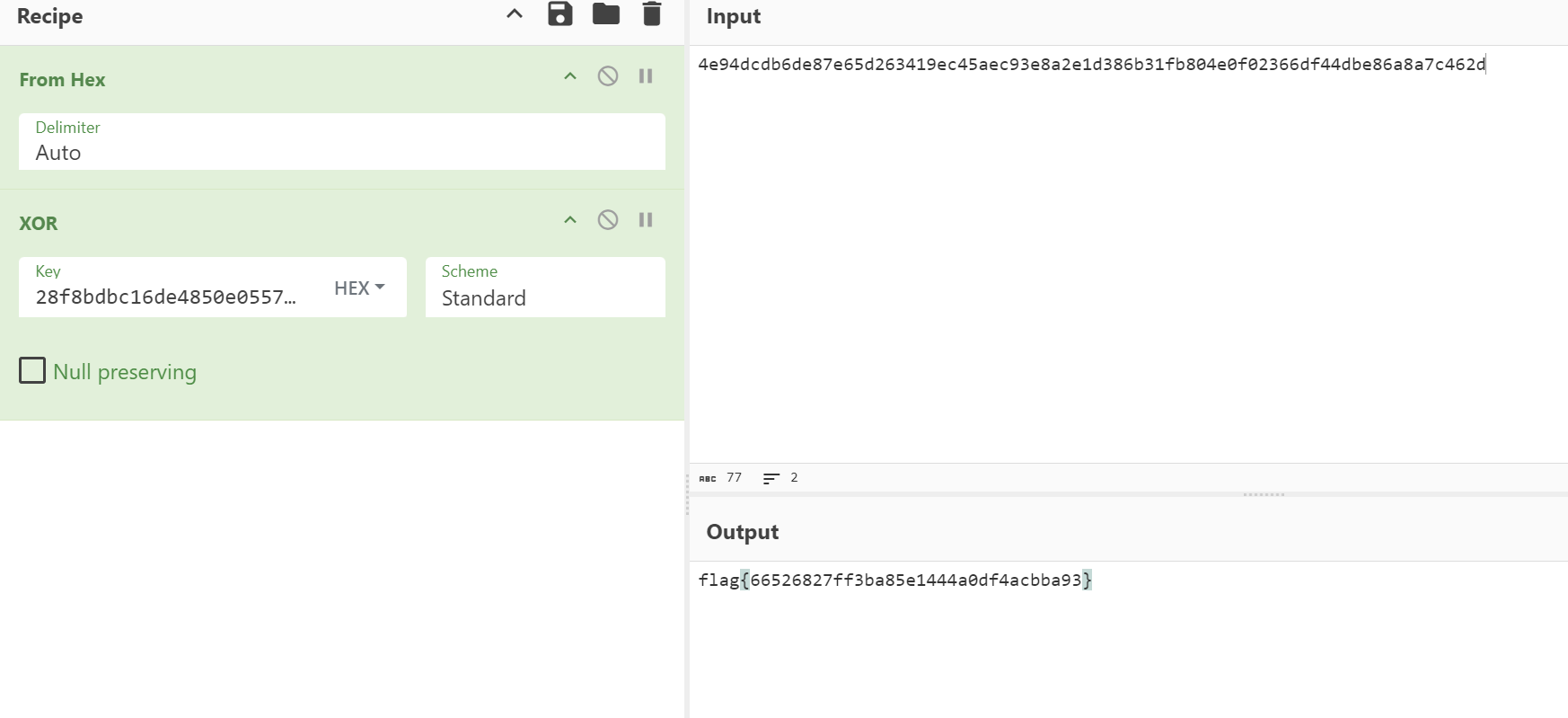
转16进制进行XOR异或
flag{66526827ff3ba85e1444a0df4acbba93}
misc4
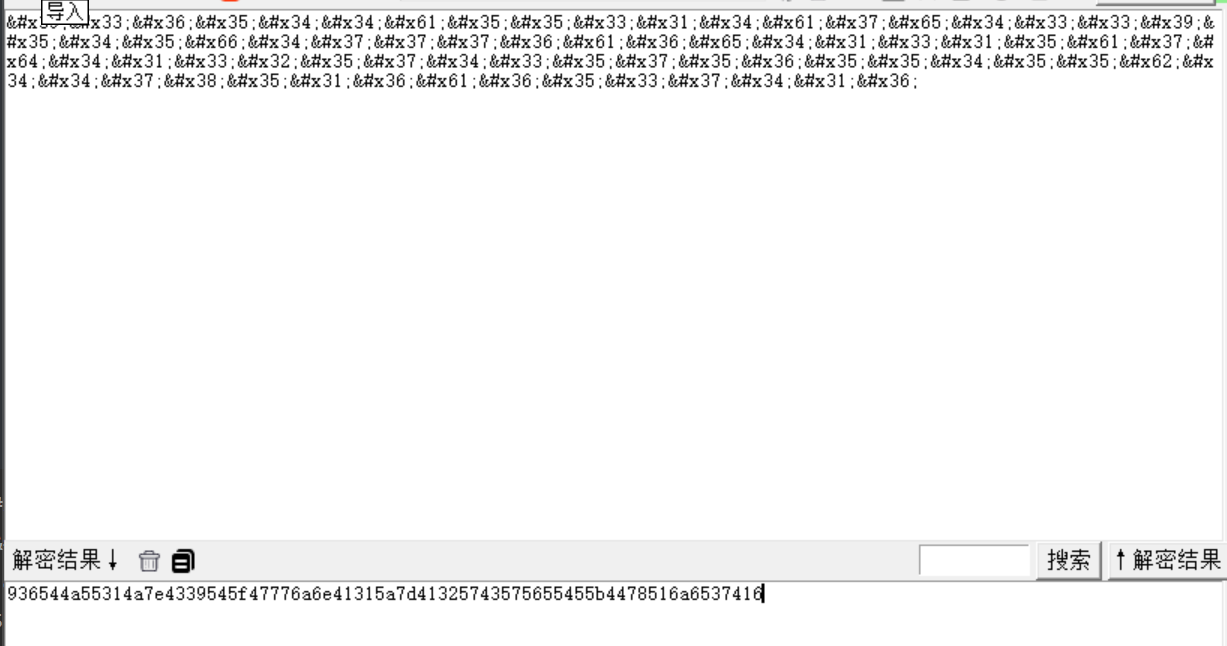
936544a55314a7e4339545f47776a6e41315a7d41325743575655455b4478516a6537416 |
很明显的一段unicode解码,随波逐流解码得
936544a55314a7e4339545f47776a6e41315a7d41325743575655455b4478516a6537416
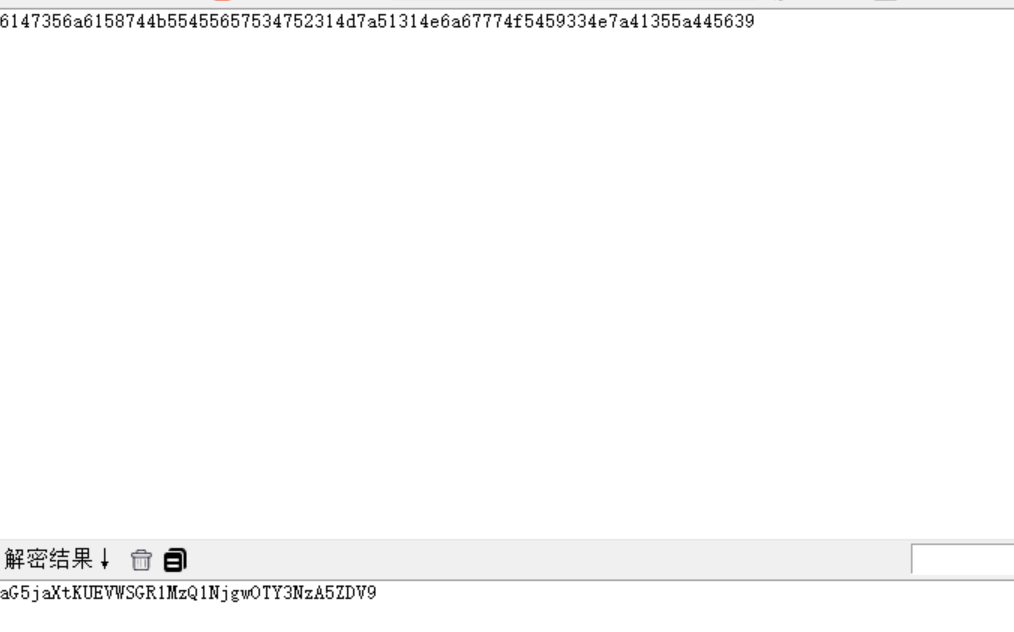
逆序得:6147356a6158744b55455657534752314d7a51314e6a67774f5459334e7a41355a445639
16机制转ascii可得
aG5jaXtKUEVWSGR1MzQ1NjgwOTY3NzA5ZDV9
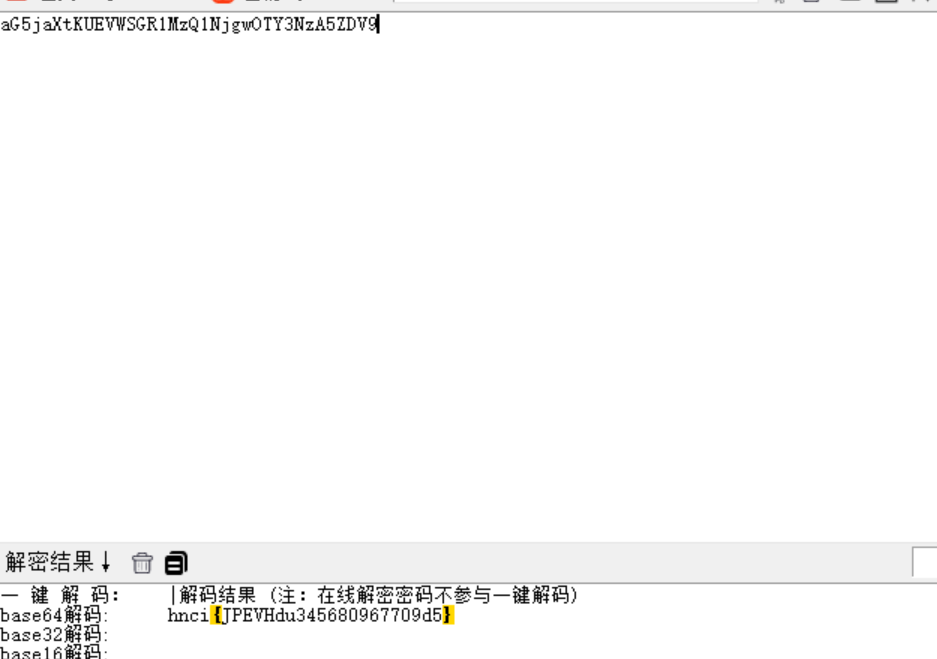
base64解密
hnci{JPEVHdu345680967709d5}
可以观察到hnci与flag之间h向后退了2格,根据f->h,l->n,a->c,g->i
我们可以得出flag
flag{HNCTFbs345680967709b5}